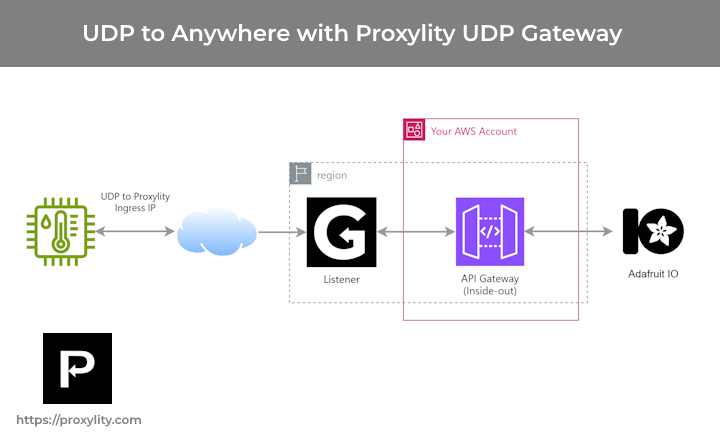
What if your smallest UDP-based IoT sensors could send data directly to cloud platforms like Adafruit IO? What if UDP monitoring systems could trigger workflows in the Zapier automation platforms? What if legacy protocols could integrate with modern REST APIs, keeping your developers in the environment they know -- all without managing servers or protocol translation?
With Proxylity's new API Gateway destination support, UDP traffic can now be directed to any HTTP/HTTPS endpoint, unlocking integration patterns that were previously impractical. We've built a complete working example with Adafruit IO, and the same architectural pattern to a broad array of cross-cloud integrations, automation platforms, and custom webhooks.
The Missing Bridge
UDP and HTTP live in different worlds. UDP excels at low-latency, low bandwidth, stateless communication and is perfect for IoT sensors, gaming, network monitoring, and a variety of enterprise protocols. HTTP dominates modern APIs, cloud functions, and automation platforms and is the mainstream developer choice.
Traditionally, bridging these protocols meant:
- Deploying, managing and paying for custom proxy servers 24/7
- Building protocol translation layers
- Maintaining complex networking and security configurations
Now there's a simpler way. API Gateway destinations act as a serverless protocol bridge, handling the UDP-to-HTTP translation while leveraging AWS's managed infrastructure.
Inside-Out Integration
The architecture is elegantly simple:
- UDP client sends packet to Proxylity listener
- Proxylity routes packet to API Gateway destination (with IAM auth)
- API Gateway transforms the request and calls external HTTP endpoint
- External service processes and returns HTTP response
- Response flows back through API Gateway to UDP client
This "inside-out" pattern means your UDP infrastructure can reach external services without exposing inbound HTTP endpoints or managing VPN tunnels. The security boundary stays intact—you control exactly which external APIs can be invoked via IAM policies.
Cross-Cloud Integration Unlocked
IoT Sensors Meet Cloud Platforms
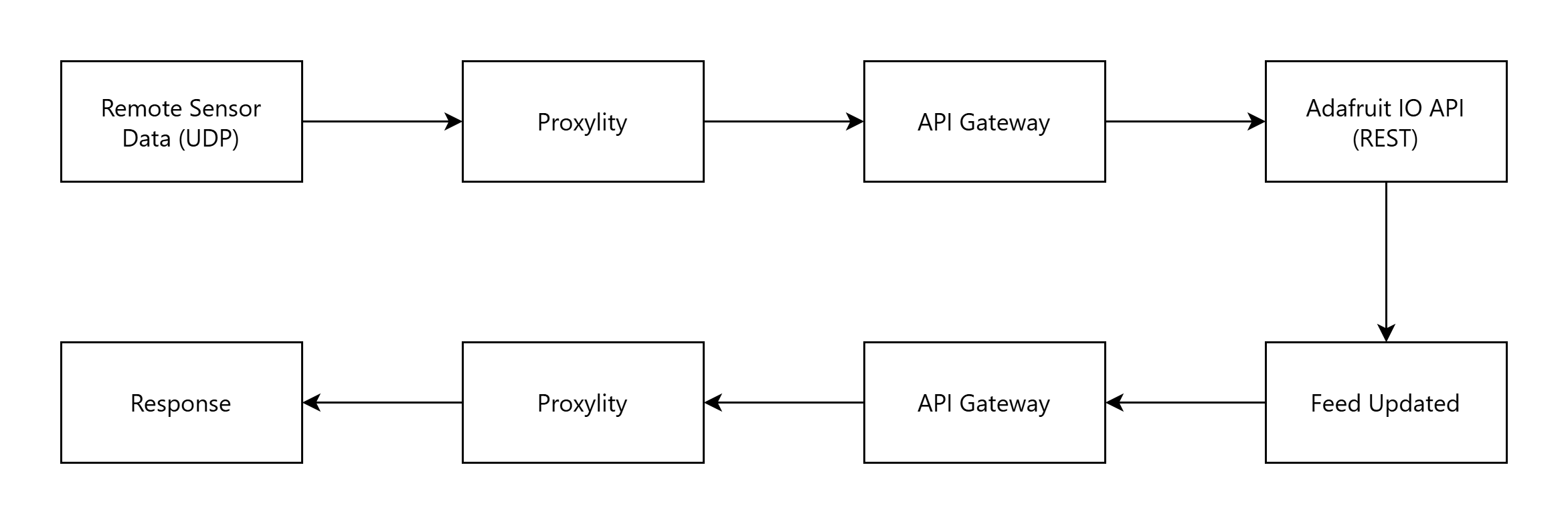
Our example implementation demonstrates UDP-to-HTTP integration with Adafruit IO, an IoT backend platform with dashboarding and actions. The complete example shows how environmental sensors can send UDP data directly to Adafruit IO feeds for visualization and triggering workflows, all defined in CloudFormation with no servers or runtime code to manage.
The pattern is straightforward:
The Same Pattern Works With GCP
The Adafruit IO integration proves the architecture. The same pattern could work with Google Cloud Platform—imagine IoT sensors deployed across manufacturing facilities, sending UDP telemetry data that triggers GCP's Vertex AI for ML-powered anomaly detection.
With API Gateway destinations:
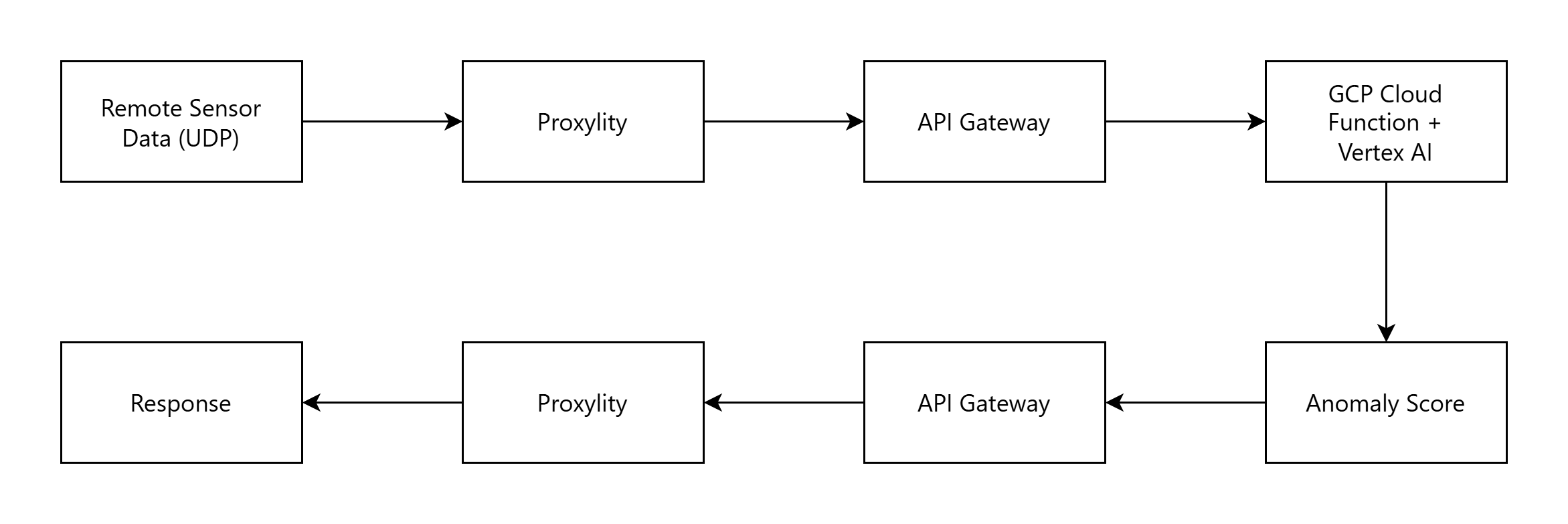
No protocol translation servers. No cross-cloud VPN setup. Just configure API Gateway's HTTP integration to point at your Cloud Function's HTTPS endpoint, add IAM permissions, and deploy.
The VTL transformation in API Gateway handles schema mapping:
#set($packet = $input.path('$.Messages[0]'))
{
"sensor_id": "$packet.Remote.IpAddress",
"timestamp": "$packet.ReceivedAt",
"telemetry": "$util.base64Decode($packet.Data)",
"facility_id": "$context.requestId"
}Your GCP function receives clean, structured JSON—unaware it originated from a UDP packet.
Azure Functions from the Edge
Similar patterns work with Azure. UDP-based network monitoring tools can trigger Azure Logic Apps for incident response workflows, or invoke Azure Functions for custom processing:
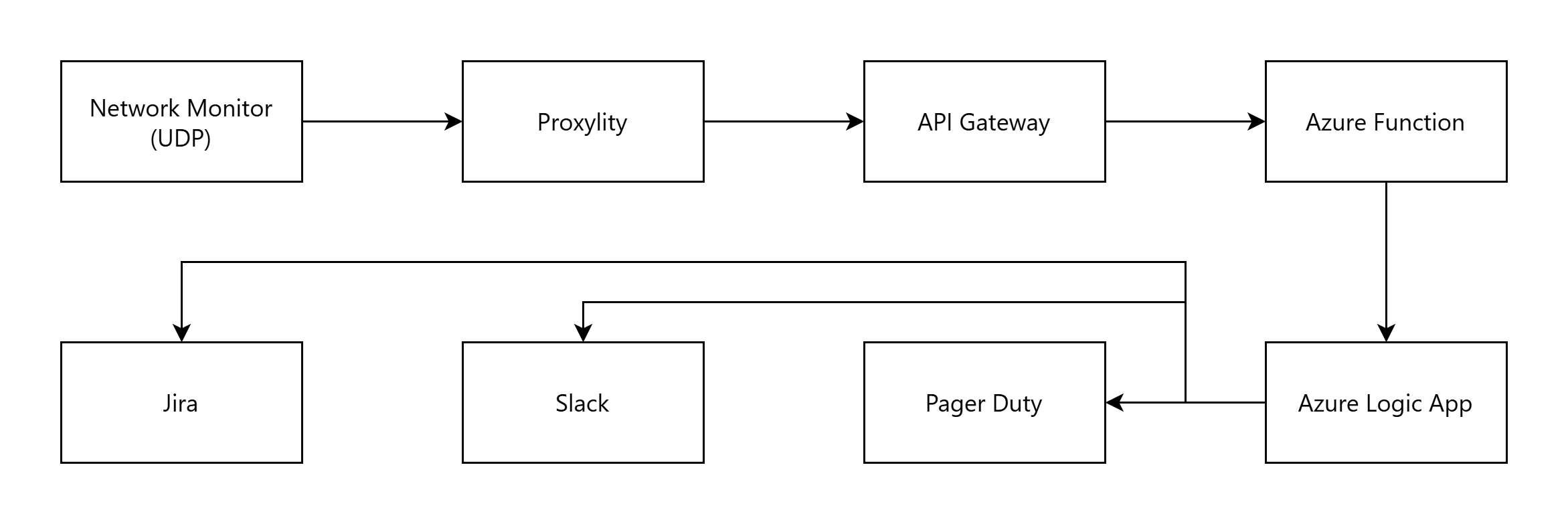
The power here isn't just protocol translation—it's the ability to compose services across cloud providers without vendor lock-in. Your monitoring stays in AWS where you have data residency requirements, but incident workflows leverage your existing Azure investments.
Automation Platform Integration
Zapier Workflows from UDP
SYSLOG messages triggering Zapier workflows? Absolutely.
The same pattern used for Adafruit IO can be applied to other automation platforms. Configure a Zapier or IFTTT webhook trigger, point API Gateway at it, and every SYSLOG message can:
- Create Jira tickets for critical errors
- Post to Slack channels
- Update Google Sheets for reporting
- Send email summaries via SendGrid
- Trigger any of 5,000+ app integrations
The VTL template extracts the syslog severity and message:
#set($log = $util.base64Decode($input.path('$.Messages[0].Data')))
{
"severity": "$log.substring(1,2)",
"message": "$log.substring($log.indexOf('>') + 1)",
"timestamp": "$input.path('$.Messages[0].ReceivedAt')",
"source": "$input.path('$.Messages[0].Remote.IpAddress')"
}Zapier receives webhook calls matching its expected schema, completely abstracted from UDP origins.
Make, n8n, and Custom Automation
The same architectural pattern works with:
- Make (Integromat): Complex multi-step workflows with data transformation
- n8n: Self-hosted workflow automation with full control
- Power Automate: Microsoft ecosystem integration
Each platform expects HTTP webhooks, and API Gateway handles the translation from UDP seamlessly.
Real-World Use Case: Game Server Monitoring
Consider a game studio running multiplayer servers across AWS regions. Game servers emit UDP metrics (player counts, latency, match results) every second. The development team built a real-time monitoring dashboard as a custom UDP server app and deploy and maintain it on a fleet of VMs.
Before: EC2 instances running custom UDP servers in each region, converting game server metrics to HTTP for posting to dashboards. Operational overhead: always on costs, patching, monitoring, scaling the fleet.
After: API Gateway destination pointing at the dashboard's webhook endpoint. VTL template transforms UDP packets into the dashboard's expected JSON format. Operational overhead: zero.
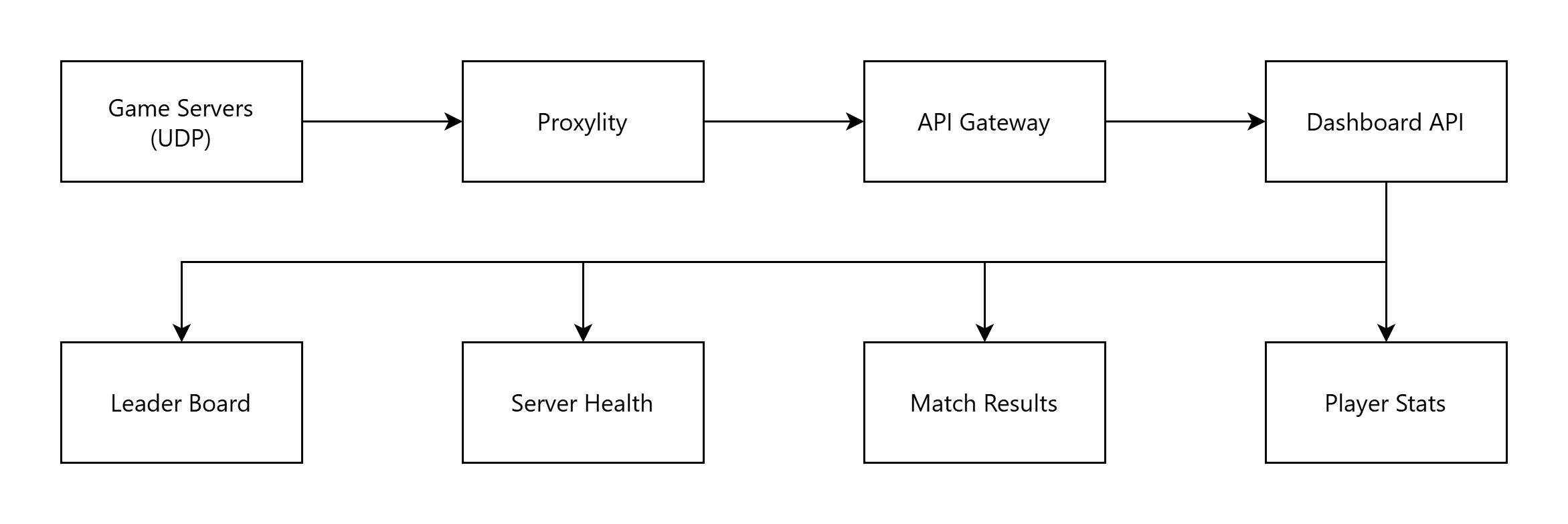
IAM-Secured External Calls
Here's what makes this pattern particularly powerful: fine-grained IAM control over external service access.
Unlike webhook URLs (security through obscurity) or API keys (shared secrets to rotate), IAM policies provide resource-level permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowAdafruitIO",
"Effect": "Allow",
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:us-east-1:123456789012:xyz/prod/POST/adafruit/*"
},
{
"Sid": "AllowCustomDashboard",
"Effect": "Allow",
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:us-east-1:123456789012:xyz/prod/POST/dashboard"
}
]
}This policy explicitly authorizes calling Adafruit IO feeds and a custom dashboard endpoint. Any attempt to invoke other routes, even if someone discovers the API Gateway URL, fails at the IAM layer.
Benefits:
- Auditable: Every invocation logged to CloudTrail
- Revocable: Update policy to instantly cut off access
- Granular: Per-endpoint, per-stage, per-method permissions
- No secrets: IAM role assumption, zero credential sharing
Debugging Multi-Cloud Flows
When UDP packets flow through API Gateway to external services, debugging requires visibility at multiple layers.
Three-Layer Observability
Layer 1: UDP Payload Capture
Use composite destinations to log original UDP packets to CloudWatch Logs before transformation:
Destinations:
- Name: gcp-function
DestinationArn: arn:aws:execute-api:...
- Name: udp-debug
DestinationArn: arn:aws:logs:us-east-1:123456789012:log-group:/debug/udpLayer 2: API Gateway Execution Logs
Enable CloudWatch logging in API Gateway to see VTL transformations, backend calls, and responses:
MethodSettings:
- LoggingLevel: INFO
DataTraceEnabled: true # Full request/response bodiesLayer 3: External Service Logs
Check the destination service's native logging (Adafruit IO activity logs, or Cloud Logging for GCP, Application Insights for Azure, Task History for Zapier in potential future integrations).
With all three layers visible, you can trace a single UDP packet's journey from sender → Proxylity → API Gateway → external API → response → back to sender.
HTTP API vs REST API: When to Use Each
AWS API Gateway offers two types, each suited to different scenarios:
HTTP API: Simple Passthrough
- Best for: Services you control that can accept Proxylity's JSON packet format
- Advantages: 71% cheaper, lower latency, simpler setup
- Limitation: Minimal transformation—what Proxylity sends is what the backend receives
REST API: Full Transformation
- Best for: Third-party APIs, SaaS platforms, external services with specific schemas
- Advantages: VTL templates for request/response mapping, header manipulation, complex transformations
- Reality: Most external integrations require REST API for schema adaptation
In practice, unless you're calling a custom service that accepts Proxylity's standard packet format, you'll use REST API for the transformation capabilities.
Getting Started
Ready to bridge UDP to HTTP? The udp-to-http folder in our examples repository includes a complete working example:
- Adafruit IO Integration: Send UDP sensor data to Adafruit IO feeds with complete CloudFormation template, IAM roles with least-privilege permissions, and VTL mapping template
This example demonstrates the full pattern that can be adapted for other external services like GCP Cloud Functions, Azure webhooks, Zapier triggers, or custom APIs. The architectural approach remains the same—only the VTL transformation and endpoint URL change.
For comprehensive guidance on external integrations, security patterns, and debugging workflows, see the Integrating Outside AWS documentation.
What This Unlocks
UDP-to-HTTP bridging isn't just about protocol translation—it's about architectural flexibility.
You can now:
- Integrate legacy UDP systems with modern cloud-native services
- Build multi-cloud architectures without vendor lock-in
- Leverage best-of-breed services across AWS, GCP, and Azure
- Connect UDP devices to automation platforms without infrastructure
- Implement hybrid cloud patterns with on-premises HTTP services
- Trigger external workflows from network events and monitoring data
All without managing servers, protocol proxies, or complex networking.
The cloud isn't one vendor's walled garden—it's an ecosystem of services across providers and platforms. API Gateway destinations make that ecosystem accessible to UDP-based systems, opening integration possibilities that were previously too costly or complex to implement.
What will you build?